What Is IT/OT Convergence?
What Is IT/OT Convergence?
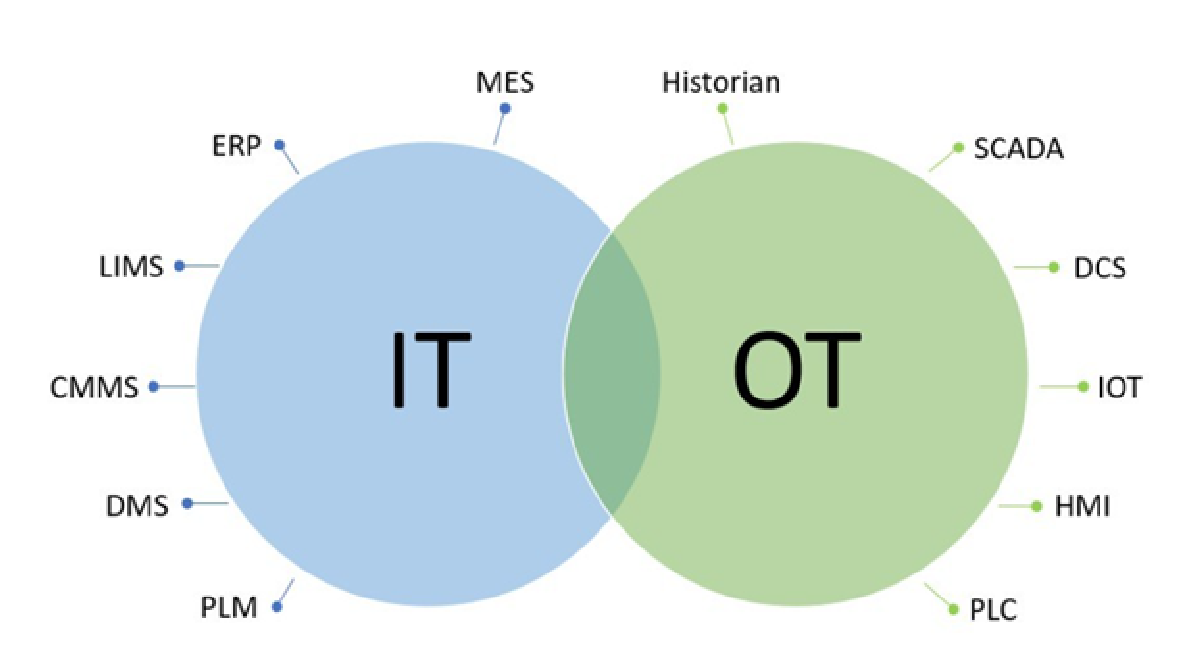
IT/OT convergence is the integration of data management systems (IT) with industrial operation systems (OT). This integration allows for real-time data exchange, enhancing the efficiency and effectiveness of both systems. Industries benefit from improved decision-making and operational processes, grounded in accurate, timely data.
What Is OT?
Operational Technology (OT) refers to the combination of hardware and software designed to manage, control, and oversee physical equipment and processes in sectors like manufacturing, energy, and telecommunications.
It utilizes technologies including Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems to oversee, manage, and automate industrial activities in real time. Although legacy systems are still prevalent in OT, there is a noticeable shift towards more contemporary integrations due to technological advancements.
OT plays a crucial role in amplifying the efficiency, security, and dependability of industrial processes. It achieves this by offering instantaneous feedback and control mechanisms, reducing downtime and boosting output.
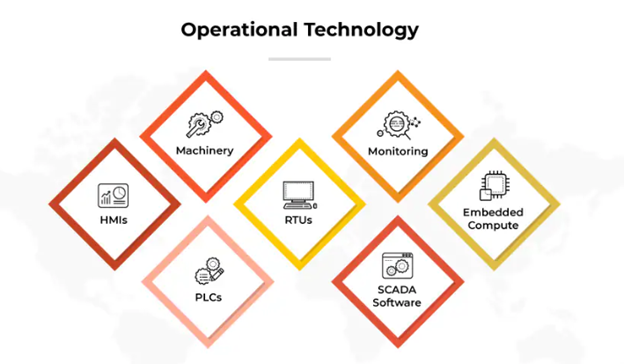
Distinct from Information Technology (IT), OT is characterized by its direct engagement with industrial machinery and procedures, with a concentration on tangible environments and operational necessities.
What Is the Difference Between IT and OT?
IT and OT serve distinct roles within an organization. IT is primarily concerned with managing and processing data to ensure its availability, confidentiality, and integrity. Its domain includes computers, servers, and similar devices that handle data storage, retrieval, and transmission tasks. OT, on the other hand, is tasked with controlling and monitoring physical processes and equipment, ensuring operational effectiveness and safety within industrial settings.
The environments in which IT and OT operate are markedly different. IT functions within a general computing environment and deals with standard operating systems for data-centric tasks. In contrast, OT is tailored for industrial settings, employing specialized, often proprietary systems to meet specific operational requirements.
Security considerations also vary. IT security emphasizes data confidentiality, while OT security is centered on the safety and availability of physical processes and equipment. System maintenance and updates in IT are frequent and regular, whereas OT prioritizes uninterrupted operation, scheduling updates during specific maintenance windows to avoid operational disruptions.
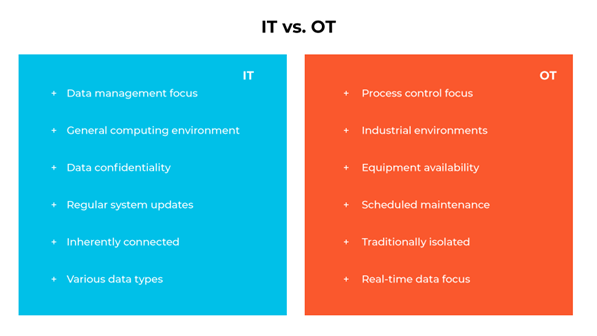
Connectivity and data use and processing distinguish IT and OT as well. IT is characterized by its connectivity, enabling data exchange and communication over networks. OT has traditionally been more isolated but is becoming increasingly connected due to the integration of Industrial Internet of Things (IIoT) technologies. While IT handles a diverse range of data types and focuses on broader business data needs, OT is concentrated on real-time data processing essential for monitoring and controlling industrial equipment and processes. The specific and immediate use of data in OT is crucial for maintaining operational efficiency and safety.
How and Why IT and OT Are Converging?
Traditionally, Information Technology (IT) and Operational Technology (OT) have existed in separate domains within organizations, each performing distinct functions. However, a transformation is underway, characterized by the systematic integration of these two previously isolated worlds, leading to what is known as IT/OT convergence.
This convergence is propelled by digital transformation and advances in technologies like the Internet of Things (IoT) and big data analytics. The merging of IT and OT enables a seamless flow of data between the digital and physical worlds, bridging the gap between data management systems and industrial operations. The digital information world can now not only visualize but also influence the physical operational world, leading to enhanced efficiency and innovation in business processes.
One of the core advantages of IT/OT convergence is increased efficiency. It facilitates the integration of different technologies to work as a single, cohesive system, reducing errors and enhancing workflows. This integration means that data from physical operations (OT) can be quickly analyzed and influenced by IT systems, allowing for more informed decision-making and autonomous operation which improves accuracy and uptime.
The core of IT/OT convergence is the ability to enhance the value delivered by both IT and OT systems. It fosters a level of interconnectivity that streamlines operations, fosters innovation, and introduces new services. This integration is becoming increasingly pivotal in the era of Industry 4.0 and IIoT.
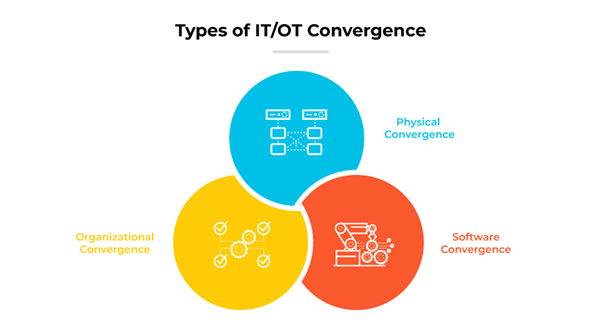
IT/OT convergence is not a monolithic concept, but a multifaceted initiative tailored to the specific organizational needs and goals. Each type of convergence—physical, software, and organizational—addresses distinct aspects of the integration process. For example, this includes direct connection of devices, seamless data flow, and the harmonization of organizational workflows.
The Role of IoT and IIoT in IT/OT Convergence :-
The advancement of the Internet of Things (IoT) and Industrial Internet of Things (IIoT) significantly influences IT/OT convergence.
Traditional OT devices, such as sensors, were not designed for network connectivity. This limits their function to data collection without the ability to transmit this data over a network. IoT devices are networked computing entities. They are adept at collecting, transferring, and analyzing data, and play a pivotal role in facilitating IT/OT convergence.
In the industrial context, IIoT enhances the potential of IT/OT convergence by empowering OT devices with real-time data processing capabilities. This transformation is realized through the incorporation of smart sensors on industrial equipment, enabling these devices to collect and transmit data to IoT hubs or gateways. For example, on a factory floor, enhanced sensors can gather operational data and relay it over wireless networks to back-end system applications. Applications then interpret data to inform immediate actions, such as equipment maintenance, ensuring timely interventions and minimizing downtime.
The synergy of IoT and edge computing amplifies the efficacy of IT/OT convergence in industrial settings. Edge computing allows IIoT devices to process data in real time closer to the source. This reduces the need to transmit vast amounts of data over networks to centralized locations for processing. This capability is crucial in distributed network architectures common in industrial environments. In industrial environments, immediate data insights are essential for monitoring.
IT/OT Security Convergence :-
As IT and OT environments converge, there’s an adjacent convergence of IT and OT security.
Traditionally, IT security focuses on protecting data and maintaining the confidentiality, integrity, and availability of information. OT security is more concerned with ensuring the availability, integrity, and reliability of industrial processes in addition to the safety of human lives and the environment.
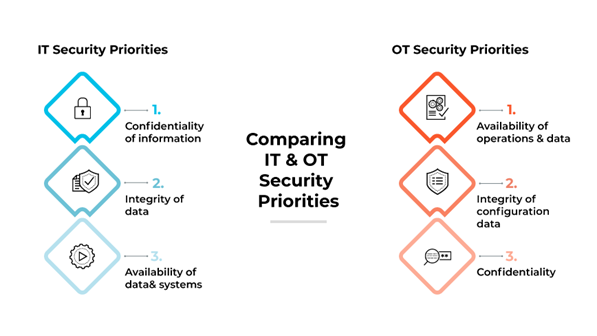
In the context of IT/OT convergence, security must be holistic, addressing vulnerabilities and risks inherent in both environments. This convergence involves the integration of security policies, practices, and technologies to protect the entire organization's ecosystem, covering data and industrial processes. This is important because as OT systems become more connected, they become more vulnerable to cyber threats that have traditionally targeted IT systems. A unified approach to security that covers both IT and OT environments is critical in today's interconnected, increasingly digital world.
IT/OT convergence brings about significant efficiency and data utilization advancements, but also introduces security challenges. With IT systems designed for data processing and OT focusing on the control of physical processes, their convergence creates a complex landscape. Security protocols of one may not seamlessly integrate with the other. The integration often exposes OT to cybersecurity threats, increasing the need for comprehensive security strategies that encompass both realms.
A notable challenge stems from OT systems’ enduring nature compared to the shorter lifecycle of IT infrastructures. OT systems are designed to last decades. Because of this, they often lack the built-in security features inherent in their IT counterparts. A prolonged lifecycle, coupled with proprietary designs, complicates advanced security protocol integration. The legacy nature necessitates thorough security assessments, and in some instances, comprehensive upgrades to meet converged environment security demands. Updates frequently require revisiting the concept of air gapping – the division between operational technology and IT systems that are connected to the internet.
The continuous, mission-critical nature of OT systems poses further security complexities. OT environments often cannot afford downtimes for updates or maintenance without incurring substantial operational and financial impacts. This can sometimes lead to postponed security updates, which creates vulnerabilities. The incorporation of IoT and IIoT enhances real-time data processing and analytics but also expands the attack surface for potential cyber threats.
For secure IT/OT integration, security strategies must evolve to safeguard the integrity, confidentiality, and availability of data. Organizations must balance the need for operational continuity with stringent security protocols.
IT/OT Convergence Benefits :-
The fusion of IT and OT is a practical response to the demand for increased efficiency and innovation in various industries. By aligning data analytics with core operational processes, organizations are achieving measurable improvements and overcoming complex challenges. This synergy is proving essential for cost reduction, improved decision accuracy, and adherence to regulatory standards.
IT and OT integration involves navigating through a complex terrain of technological and organizational complexities. It demands a blend of varied technologies and unification of diverse professional cultures and operational standards.
IT/OT Convergence Best Practices :-
Security Concerns
OT systems vulnerability during IT integration poses a significant challenge due to increased risks of data breaches and industrial espionage. The combination of legacy OT systems with IT networks exposes larger attack surfaces.
Impacts of IT/OT Convergence on ICS Security :-
With the arrival of IIoT, every ICS sensor, instrument and device accessible over an IT/OT network is susceptible to weaponization. ICS sensors can be vulnerable to botnets used to launch targeted attacks on critical infrastructure. This includes energy grids, power plants, water and waste management systems, food processing plants, and transportation networks.
The human-machine interface (HMI) that connects operators to industrial control systems are also typically networked to various IT infrastructures. Accessibility to HMIs from internet-facing business networks poses a risk to ICS security, making HMIs susceptible to IP-based vulnerabilities. IP-based vulnerabilities can include authentication bypass, weak session management, unsecured ICS communication protocoling and insufficient control traffic encryption.
Attackers typically infiltrate ICS systems with both generic malware and malware designed specifically to target and attack critical infrastructure. These infiltrations often result in denial-of-service, or DoS, attacks that paralyze or halt industrial operations. ICS and connected IIoT devices are also high-value targets for hackers looking to collect ransoms or sabotage rival nations by gaining access to confidential data.
ICS security breaches come with vastly different consequences than standard breaches. The severe impacts of a cyberattack can include disabling a city's power grid, triggering an explosion in a nuclear plant by undermining safety systems, or rerouting sewage into an urban area's water supply.
Common ICS threats :-
Several common threats pose risks to Industrial Control Systems (ICS), potentially leading to operational disruptions, safety incidents, or unauthorized access to critical infrastructure. Some of the most prevalent ICS threats include :
- Malware : Malicious software targeting ICS environments can disrupt operations, steal sensitive information, or provide unauthorized access to attackers. Examples include ransomware, which can encrypt critical files or systems, and Trojans designed to exfiltrate data or provide remote access to attackers.
- Denial of Service (DoS) Attacks : DoS attacks aim to overwhelm ICS networks or systems with excessive traffic, rendering them unavailable to legitimate users. This can disrupt operations and lead to downtime in critical infrastructure systems.
- Insider Threats : Malicious insiders or negligent employees pose significant risks to ICS security. Insiders may intentionally sabotage systems, steal sensitive information, or inadvertently compromise security through careless actions, such as connecting unauthorized devices to the network or falling victim to phishing attacks.
- Supply Chain Attacks : Attackers may target third-party vendors, suppliers, or contractors associated with ICS environments to infiltrate networks or introduce malicious components into the supply chain. Compromised software updates or counterfeit hardware can introduce vulnerabilities and compromise system integrity.
- Unauthorized Access : Unauthorized access to ICS networks, systems, or devices can occur through weak authentication mechanisms, misconfigured access controls, or exploiting software vulnerabilities. Attackers gaining unauthorized access can manipulate industrial processes, steal sensitive data, or cause physical damage to equipment.
- Data Breaches : Breaches of sensitive data within ICS environments can compromise the confidentiality, integrity, and availability of critical information. This may include proprietary process data, operational details, or personally identifiable information (PII) of employees or customers.
- Physical Threats : Physical attacks on ICS infrastructure, such as tampering with equipment, sabotaging facilities, or disrupting power supplies, can cause significant disruptions to operations and compromise safety.
- Social Engineering : Attackers may use social engineering techniques, such as phishing emails, pretexting, or impersonation, to manipulate employees into divulging sensitive information, providing unauthorized access, or executing malicious actions within ICS environments.
- Zero-Day Exploits : Zero-day vulnerabilities, for which no patch or mitigation is available, can be exploited by attackers to compromise ICS systems. Attackers may exploit unknown vulnerabilities to gain unauthorized access, execute arbitrary code, or disrupt operations.
- Legacy System Vulnerabilities : Many ICS environments still rely on legacy systems and equipment with outdated software and insecure protocols. These systems may contain known vulnerabilities that can be exploited by attackers to compromise security.
Best practices for ICS security :-
Implementing effective security practices is crucial for protecting Industrial Control Systems (ICS) from cyber threats and vulnerabilities. Here are some best practices for ICS security:
- Risk Assessment : Conduct regular risk assessments to identify potential threats, vulnerabilities, and consequences to ICS environments. This helps prioritize security efforts and allocate resources effectively.
- Security Policies and Procedures : Develop and enforce comprehensive security policies and procedures tailored to the specific needs and requirements of ICS environments. This includes defining access controls, network segmentation, incident response protocols, and data protection measures.
- Access Control : Implement strong access controls to restrict unauthorized access to ICS networks, systems, and devices. This includes measures such as user authentication, role-based access control (RBAC), and multi-factor authentication (MFA).
- Network Segmentation : Segment the ICS network into zones and conduits based on the criticality and sensitivity of systems and assets. This limits the impact of security incidents and prevents lateral movement by attackers within the network.
- Endpoint Security : Secure individual devices and endpoints within the ICS environment through measures such as antivirus software, firmware updates, device hardening, and application whitelisting.
- Data Breaches : Breaches of sensitive data within ICS environments can compromise the confidentiality, integrity, and availability of critical information. This may include proprietary process data, operational details, or personally identifiable information (PII) of employees or customers.
- Network Security : Deploy firewalls, intrusion detection and prevention systems (IDPS), and security gateways to monitor and protect ICS networks from unauthorized access, malware, and cyber threats.
- Security Monitoring : Continuously monitor ICS networks and systems for signs of suspicious activity, anomalies, and security incidents. Collect and analyze log data, network traffic, and system events to detect and respond to potential threats promptly.
- Incident Response : Establish incident response plans and procedures to quickly respond to and mitigate security incidents in the ICS environment. Identify the scope and impact of incidents, contain threats, restore normal operations, and conduct post-incident analysis to prevent future occurrences.
- Employee Training and Awareness : Provide training and awareness programs for personnel who work with or have access to ICS systems. Educate employees about security best practices, policies, and procedures to reduce the risk of human error and insider threats.
- Regulatory Compliance : Ensure compliance with relevant industry standards, regulations, and guidelines related to ICS security, such as the NIST Cybersecurity Framework, ISA/IEC 62443, and sector-specific regulations.
- Vendor and Supply Chain Security : Assess and manage the security risks associated with third-party vendors, suppliers, and contractors who provide components, software, and services used in ICS environments. Implement measures to secure the supply chain and mitigate potential vulnerabilities.
- Regular Updates and Patch Management : Keep ICS systems up to date with security patches, firmware updates, and software upgrades to address known vulnerabilities and mitigate security risks.
- Physical Security : Protect physical infrastructure components of ICS systems, such as control rooms, substations, and equipment installations, from unauthorized access, tampering, and sabotage.
- Continuous Improvement : Continuously evaluate and improve ICS security measures based on evolving threats, technology advancements, and lessons learned from security incidents and breaches.
By implementing these best practices, organizations can enhance the security posture of their Industrial Control Systems and mitigate the risk of cyber threats and vulnerabilities impacting critical infrastructure operations.